Products
Onspring delivers immediate ROI
70%
increase in efficiencies
40%
of time saved
100%
connectivity across GRC
Federal Agencies Benefit from POA&M Management
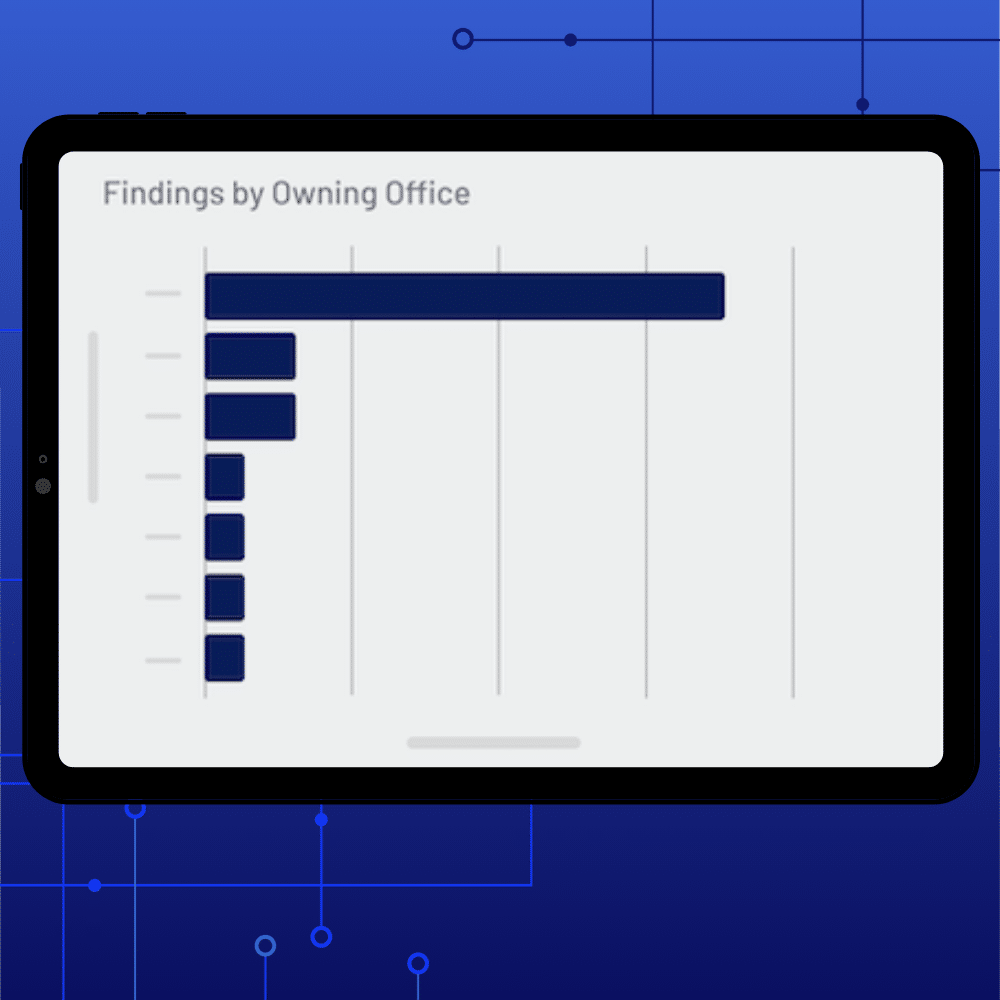
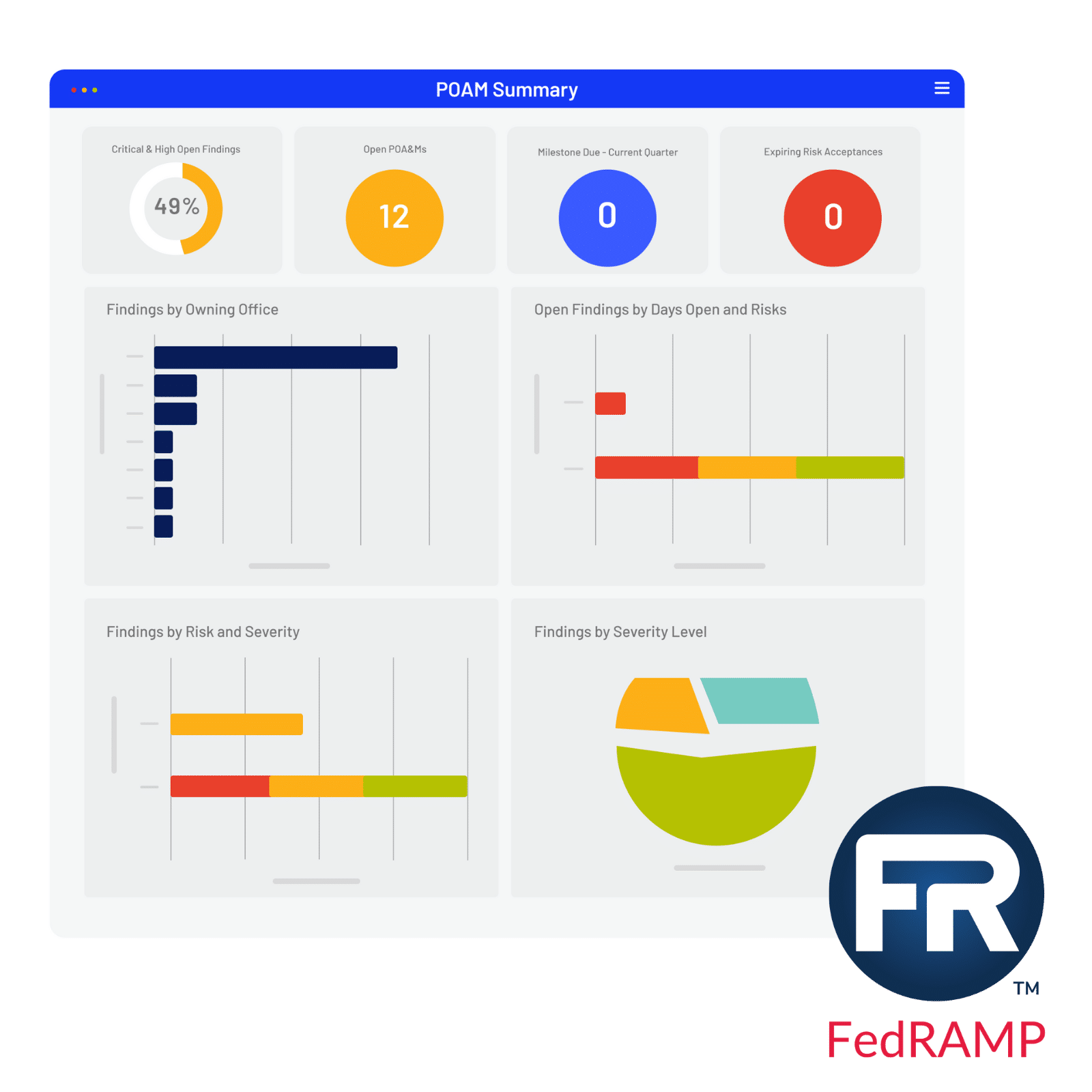
POA&M Management in Cloud-based FedRAMP Software
Integrate and manage internal and external security findings while simultaneously automating workflows, approvals, analytics, and continuous monitoring. Deliver real-time status and evidence against scheduled completion dates for milestones with cost summaries.
Centralized Weakness Aggregation
- Consolidate all security findings. Automatically ingest weaknesses from scans, audits and continuous monitoring.
- Prioritize and categorize findings. Apply risk ratings and link to frameworks like NIST 800-53 for triage.
- Eliminate scattered spreadsheets with a unified register of all weaknesses.
Dynamic Remediation Planning
- Develop actionable corrective action plans (CAPs). Define tasks, milestones and responsibilities for each weakness.
- Automate review and approval workflows.
- Connect to vulnerability management and project management systems.
Real-time Progress Tracking
- Monitor remediation status in real-time. Track actual vs. scheduled completion for all POA&M items.
- Track resource utilization, like financial costs and operational resources for remediation.
- Receive automated notifications for deadlines, overdue tasks, or status changes.
Integrated Risk Acceptance
- Document decisions, justifications and approvals directly in the platform.
- Connect accepted risks and accepted weaknesses into your broader organizational risk register.
- Provide an auditable trail of immutable records of all risk acceptance rationales.
Automated Reporting & Audit Readiness
- Generate compliant POA&M reports instantly. Produce tailored reports for NIST, FedRAMP, CMMC, etc.
- Analyze costs and remediation trends over time or by control categories.
- Simplify audit evidence collection.
Framework Alignment
- Utilize libraries for NIST 800-53, CMMC, etc.,
- Customize workflows and reports to fit unique operational and agency needs.
- Automatically update control mappings as regulations evolve.
Onspring is FedRAMP Authorized
UEI Code: KCE8DGSLPFC8
CAGE Code: 82Z79
NAICS Codes:
- 518210 – Computing Infrastructure Providers, Data Processing, Web Hosting & Related Services
- 511210/513210 – Software Publishers
- 541511 – Custom Computer Programming Services
- 541512 – Computer Systems Design Services
- 541690 – Other Computer-Related Services
- 541519 – Other Scientific & Technical Consulting Services
Success Story
“We’ve captured and leveraged insight into the risk profile of our institution. The data we collect now is reportable across domains, so we finally have the elusive ‘single pane of glass’.”
University of Minnesota
Request a Demo to see Onspring in Action
Can we route POA&Ms through a formal approval and review process, plus capture performance management and cost metrics?
Yes. The workflow in Onspring’s POA&M software includes the full POA&M management lifecycle from identifying a weakness to analyzing the risk level, accepting risks and instigating corrective action plans, to estimating costs and completion dates, and documenting progress and results.
While the process workflow is ready-made in Onspring, you can easily adjust any step to accommodate variances specific to your agency.
Can we create a consolidated view of known issues to better understand remediation efforts, including timing, milestones and costs?
Yes. Dashboards in Onspring bring all relevant POA&M tracking information into a centralized view. This means you’ll have real-time, consolidated reporting of all known issues and can drill directly into details to understand remediation efforts, including timing, milestones and costs.
Can our agency escalate issues and see all efforts underway to close and address risks?
Yes. Onspring dashboards provide a consolidated view into all issues, which include reports to segment risks by level so your team can take a risk-based approach to issues triaging and prioritization. Automated triggers in Onspring can also be used to notify team members when high-risk weaknesses are logged. This functionality provides immediate visibility to escalate issues for remediation.
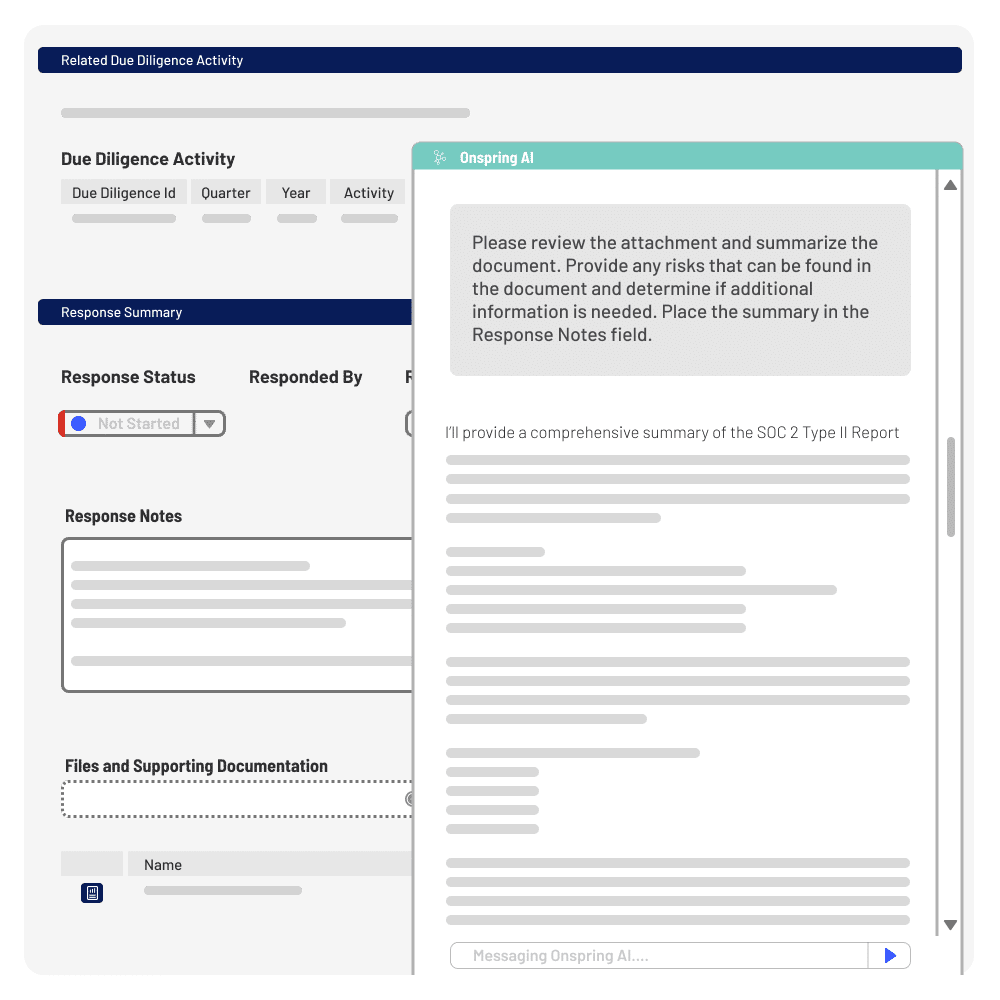
Does Onspring POA&M Management Software also manage issues generated by audit, A&A, and configuration management processes?
Onspring POA&M software can manage issues generated by audit, A&A and configuration management processes. Issues can be logged directly in Onspring by a user, or automation can ingest issues from other software, email sends and even Slack instant messages.
How does Onspring’s POA&M software reduce costs or enable faster reactions to emerging risks?
On average, customers experience 40% time savings when using Onspring and prevent hundreds of thousands of dollars in fines and costs from security deficiencies. We provide:
- Always-on live reporting eliminates time spent aggregating and formatting data for reports.
- Automated project management eliminates time spent assigning tasks, following up with owners, and keeping all stakeholders updated with costs, timelines, and open risks.
- Relational data connects weaknesses to controls, policies, and frameworks so you know every element of your agency that is impacted.
Are there guidelines for POA&M management?
Both NIST and FedRAMP offer documents to guide your POA&M process.
What if we need help configuring POA&M process in Onspring?
Onspring admin services can help you every step of the way with configuration of your POA&M management, from implementation to ongoing admin services or special builds.
Does FedRAMP require use of POA&M software?
The use of software to manage POA&M is not a legal mandate. However, businesses working under DoD contracts are required to comply with DFARS rule 252.204-7012 to protect controlled unclassified information. Ultimately, that compliance means a business must implement the cybersecurity requirements outlined in the National Institutes of Standards and Technology (NIST) 800-171 standard.
Within this standard, a business is required to systematically assess its cybersecurity risk, namely the risks associated with incomplete 800-171 compliance. Additionally, the business is also required to instill a Plan of Action and Milestones (POA&M), identifying steps that the business will carry out to mitigate those incomplete 800-171 risks.
Due to the complexities, timelines and budget, automating your POA&M management with Onspring software is often the most efficient way to streamline workflows, reporting and documentation.
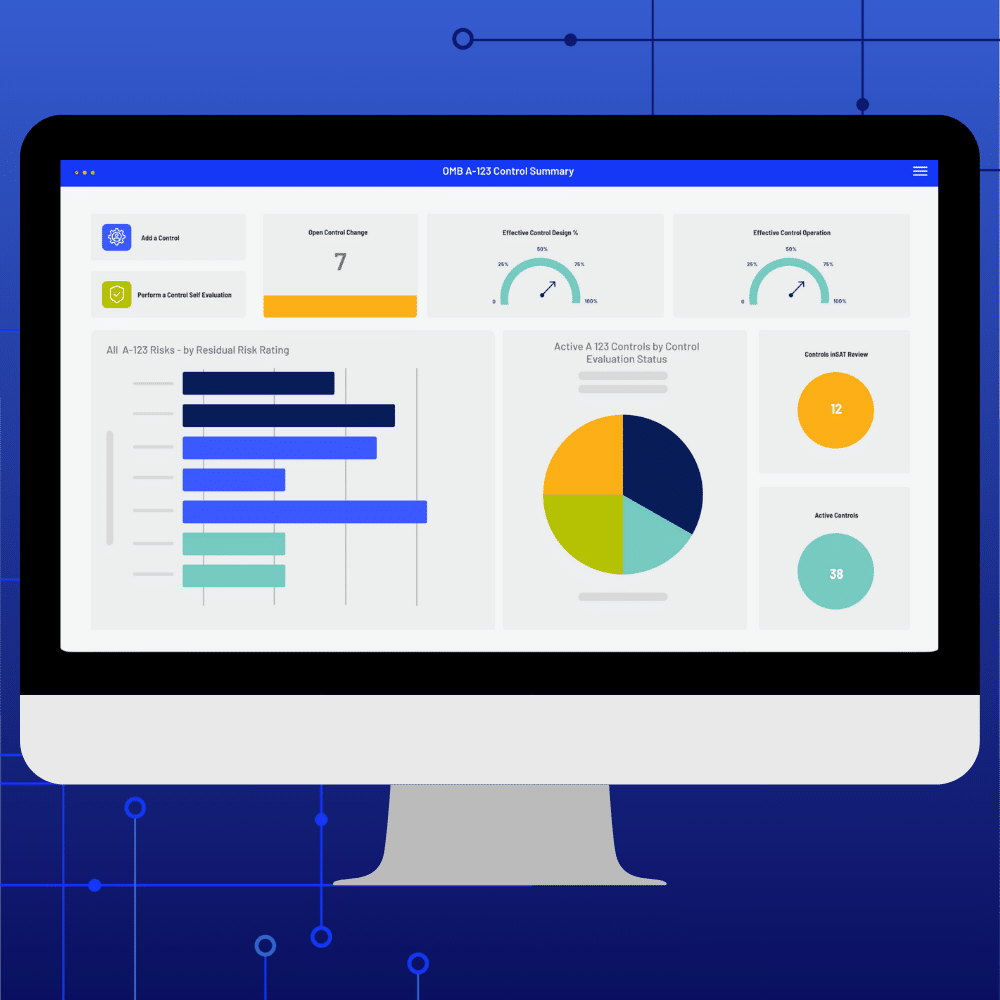
Does OMB A-123 work with POA&M?
Yes. Identify and classify deficiencies arising from control evaluation procedures, establish corrective action plans associated with Risk Evaluations & Internal Control Assessments and report on issue severity, ownership and status.
Can we implement Onspring GovCloud ourselves?
Yes. You can implement Onspring on your own once your designated administrator completes training. Training ensures success and faster implementation. The beauty of your training + our no-code platform is that anyone with knowledge of your business can implement and run point as a system administrator. No developers or IT resources are needed for implementation or updates.
If you have complex processes, we recommend consulting with our professional services team first. They can work with you to ensure optimal setup or configure solutions to fit your business needs.
Does Onspring’s GRC platform integrate with other business systems?
Yes. Onspring GRC software supports integration with systems like Docusign, Microsoft 365, Google Drive, Slack and many more. Expand Onspring’s capabilities further by integrating it with other systems through the Onspring API.
What kind of software training does Onspring offer?
Onspring offers multiple types of training, which can be combined for an ongoing learning experience:
- Onspring Essentials: This immersive class for administrators teaches the fundamentals of configuration and best practices for end-user adoption.
- Bootcamps: These focused training classes for administrators dive deep into specific Onspring features to help you achieve your goals for data management, process automation, and reporting.
- Web Training: On-demand videos are available 24/7 so you can learn to use Onspring on your schedule. Topics include configuring apps, importing data, creating surveys, using formulas, automating processes, and more.
- Free Friday Training: The name says it all. It’s free and held on Fridays twice per month. These 30-minute remote learning sessions often highlight new features so you always know what’s available for use.
Related Products
A robust set of connected programs that scale as your GovCloud GRC ecosystem expands and adapts as your business addresses change.
GovCloud GRC
- FedRamp authorized
- Automate workflows
- Real-time monitoring
OMB A-123 Compliance
- Implement a governance structure
- Connect risks to controls
- GAO-based risk assessments