Business Operations
-

Mental Health in Cybersecurity: Insights from Industry Experts
Explore the link between mental health and cybersecurity in this insightful webinar featuring Cybersecurity Director, Tamika Bass. Discover strategies to manage stress in this high-pressure industry and foster a healthier work environment.
-

The Human Firewall: Why Prioritizing Mental Health is Essential for Cybersecurity Success
With such high-stakes in cybersecurity—where constant vigilance and rapid decision-making are non-negotiable—the mental health of professionals often takes a back seat.
-
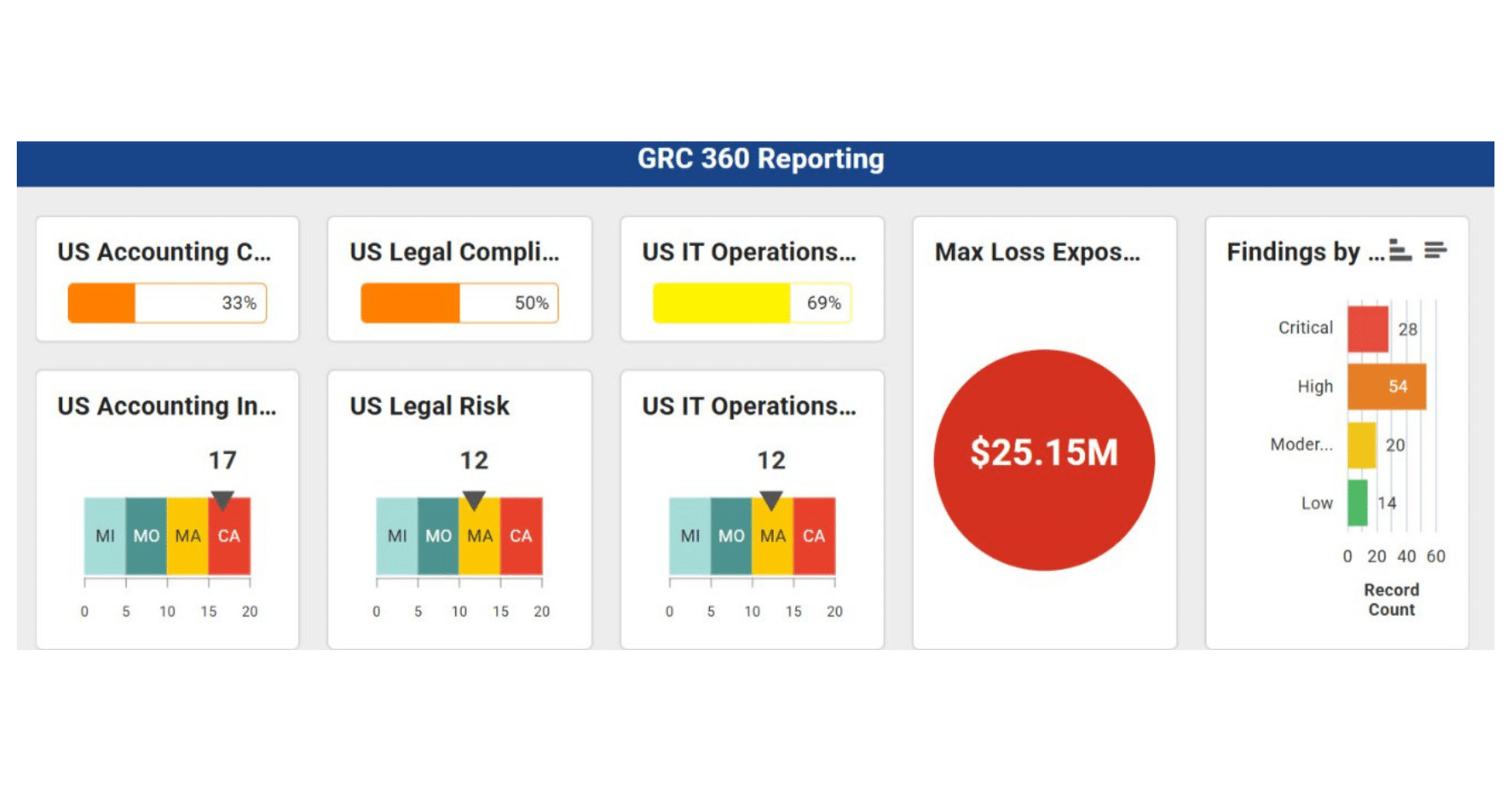
How a GRC Dashboard Can Transform Your Data
Discover how GRC dashboards can offer transparency and actionable intelligence by providing a comprehensive, real-time overview of governance, risk, and compliance activities.
-

A Quick GRC Guide to Retail Compliance Management in 2025
With AI, blockchain and evolving regulations reshaping the landscape, retail risk managers across sectors must stay agile and innovative in their compliance management this year. How well are you navigating these challenges?
-
 Compliance, Contract, GRC, Internal Audit, Policy, Regulatory Change, Risk, SOX, Third-party / Vendor
Compliance, Contract, GRC, Internal Audit, Policy, Regulatory Change, Risk, SOX, Third-party / Vendor3 Ways to Expand the Scope of Your GRC Strategy
Learn how organziations strategized and grew their GRC automations to enhance their overall governance, risk, and compliance efforts.
-

How to Present KRIs Effectively to Your Board: A Coaching Guide
Presenting KRIs effectively to your board can transform risk management from a reactive chore into proactive leadership. This guide offers step-by-step insights on aligning KRIs with business strategies, leveraging technology, and using clear communication to make your data impactful and actionable.
-

5 Signs Your SLED Agency is Ready for Automated Policy Management
Discover the 5 signs your State, Local or Education agency is ready for automated policy management to streamline compliance and efficiency.
-
3 Proven Insights for Choosing the Perfect GRC Platform
Get firsthand insights from Jennifer Plowman of TransUnion on selecting the perfect GRC platform. Learn how predictive benchmarking, real-time data and leading indicators can transform your risk management strategy.
-

3 Best Practices for Vendor Master Data Management
Learn best practices for ensuring data accuracy and establishing robust capture protocols to streamline vendor master data management.
-

DORA, The Explainer
With stringent requirements for ICT risk management and third-party oversight, the Digital Operational Resilience Act (DORA) ensures that financial entities are fortified against digital threats. Get up to speed on before the next deadline.
-
What is a Software Bill of Materials (SBOM)?
Think of a Software Bill of Materials (SBOM) as the ingredient list for your digital work, ensuring transparency and safeguarding against vulnerabilities. Learn how SBOMs can enhance compliance, streamline processes and fortify your software supply chain.
-

4 Writing Tips for Annual GRC Updating
Now is the time to refresh your GRC policies and procedures for the coming year. As you begin to write these updates, here are four tips to help boost your writing skills for better drafts and more compelling corporate narratives in your business documents.