Business Function
-

Partner Program Management – ADT Case Study
ADT expanded its use of Onspring to improve onboarding and contract management of their partner program while saving hours of time and increasing revenue.
-

HR, Legal & Compliance – Mariner Case Study
One integrated platform creating efficiencies, organization and easy management for multiple departments. Learn how Mariner brought together its Human Resources, Legal, Compliance and Marketing teams with Onspring.
-

Creating Your Vendor Management Policy
If you don’t create an all-inclusive vendor management policy, you’ll be bogged down with unending third-party management chaos triggered by different vendors.
-

The Human Firewall: Why Prioritizing Mental Health is Essential for Cybersecurity Success
With such high-stakes in cybersecurity—where constant vigilance and rapid decision-making are non-negotiable—the mental health of professionals often takes a back seat.
-

Guide: Enterprise Risk Management for Financial Institutions
Learn how Enterprise Risk Management (ERM) for financial institutions enhances decision-making, ensures regulatory compliance, and mitigates risks across various domains.
-

What is Remediation in Cybersecurity and Why Does It Matter?
Discover the importance of cybersecurity remediation in protecting your organization from cyber threats. Learn about the remediation process, key statistics, and how to implement effective strategies to enhance your security posture and ensure compliance.
-
NIST CSF vs. ISO 27001
Discover the similarities and differences between NIST CSF vs. ISO 27001 in our comprehensive guide. And find out which framework suits your business best.
-

How Automation Can Simplify Your Path to NERC Compliance
Digital tools for acheiving NERC compliance can streamline workflows, automate tasks, and deliver real-time insights—making compliance not just achievable, but efficient.
-

How to Conduct an Information Technology (IT) Risk Assessment
Learn about IT risk assessments, including how to identify vulnerabilities, enhance cybersecurity and develop effective mitigation strategies to protect your IT infrastructure from potential threats.
-

How to Create a Risk Register
Discover expert insights on how to build an effective risk register that keeps your team proactive and informed. This step-by-step guide will show you why maintaining a comprehensive risk register is worth the effort.
-
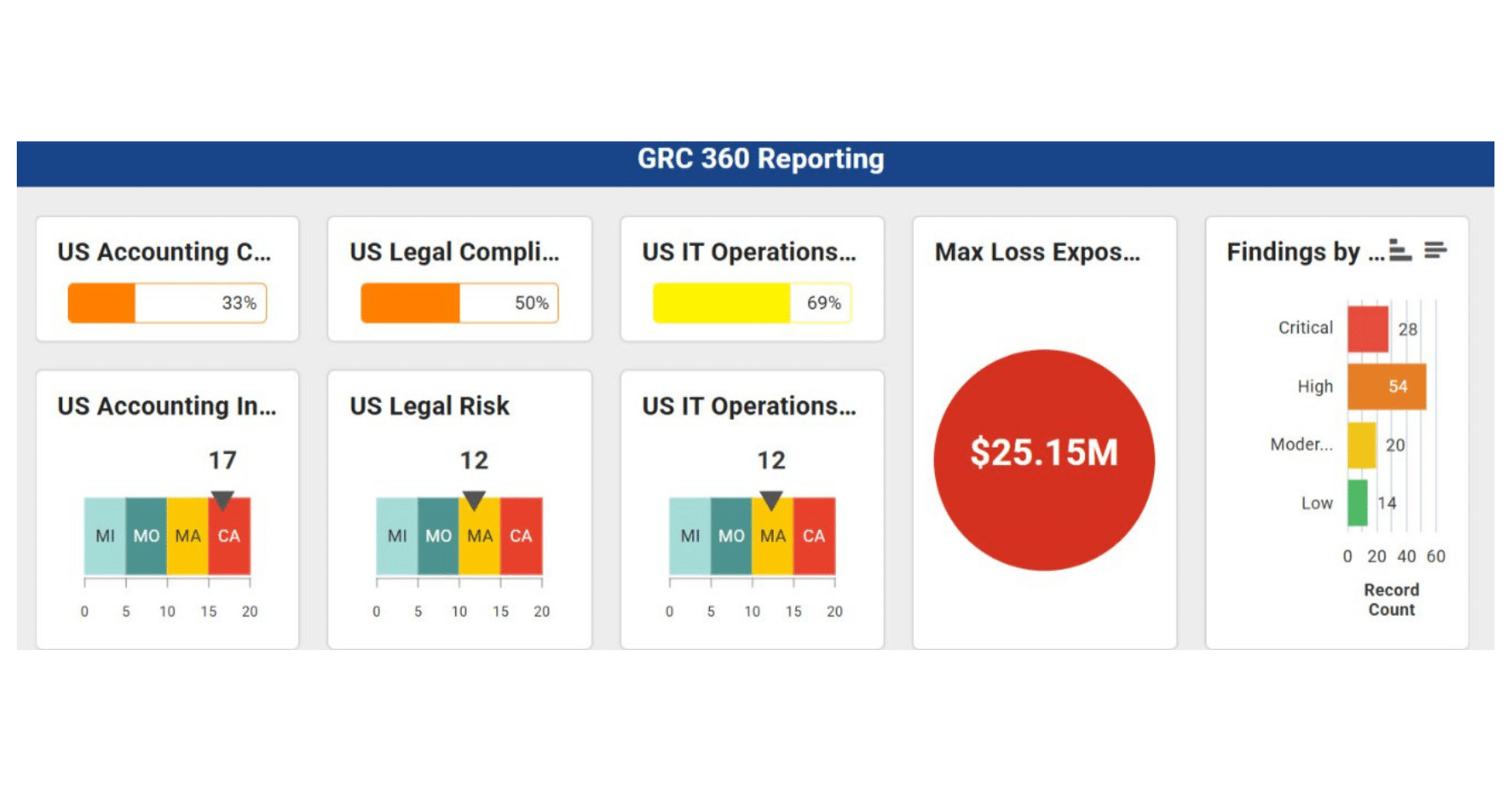
How a GRC Dashboard Can Transform Your Data
Discover how GRC dashboards can offer transparency and actionable intelligence by providing a comprehensive, real-time overview of governance, risk, and compliance activities.
-

A Quick GRC Guide to Retail Compliance Management in 2025
With AI, blockchain and evolving regulations reshaping the landscape, retail risk managers across sectors must stay agile and innovative in their compliance management this year. How well are you navigating these challenges?