Who We Serve
Empowering SLED Agencies to Automate Governance, Risk & Compliance (GRC)
When state, local and higher education organizations face increasing risks and decreasing resources, Onspring is your strategic answer. Our integrated solutions enable you to manage Governance, Risk & Compliance (GRC) effectively—moving beyond mere box-checking to digitally transformative best practices.
What Can You Expect
Onspring’s GRC platform is adaptable to any SLED organization facing increased risks and budget constraints. Our solution helps you:
Automate compliance management for state and federal regulations
Conduct risk assessments designed for public sector entities
Monitor and report on cybersecurity threats in real-time
Scale your GRC efforts without adding headcount
Comprehensive Framework Management
- Map controls across multiple compliance standards
- Seamlessly manage HIPAA, ISO, NIST and CMMC frameworks
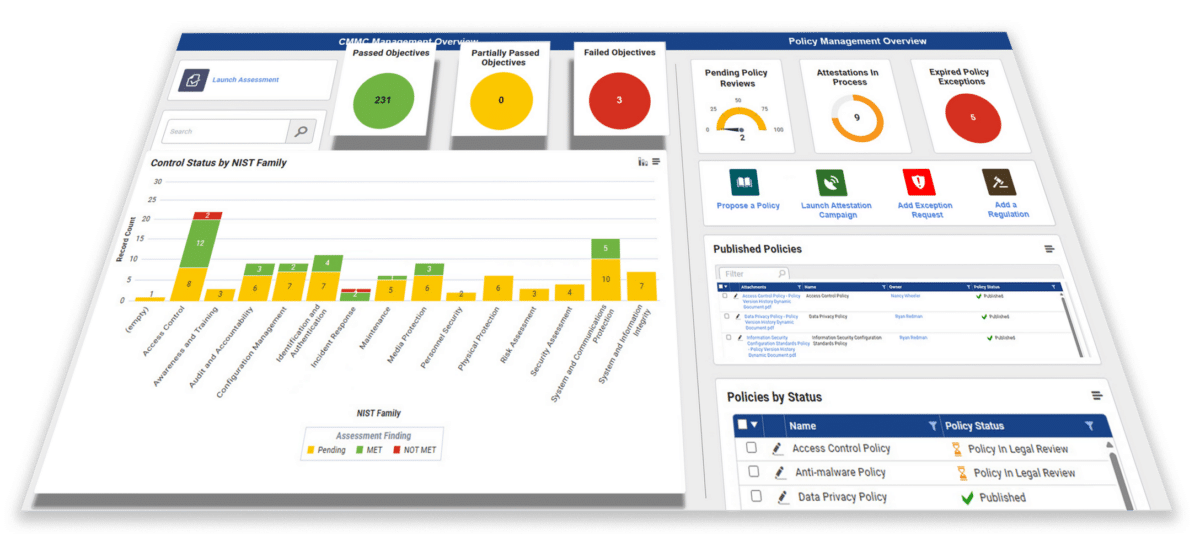
Compliance, Policy & Audit Management
- Automate lifecycle processes, compliance testing and attestations across functional groups
- Conduct efficient internal audits and manage external audit requirements
- Reduce manual effort and human error
Third-party Risk Management
- Assess, tier and track vendors efficiently
- Integrate criticality ratings from cyber and financial monitoring services
- Monitor and track Higher Education Community Vendor Assessment Toolkit (HECVAT) assessments

Compliance, Policy & Audit Management
- Automate lifecycle processes, compliance testing and attestations across functional groups
- Conduct efficient internal audits and manage external audit requirements
- Reduce manual effort and human error
Success Stories
“Prior to Onspring, we were utilizing separate tools, emailing each other back and forth and using Excel spreadsheets to communicate updates.”
Warner Bros. Discovery

FAQs
- Always-on live reporting eliminates time spent aggregating and formatting data for reports.
- Automated project management eliminates time spent assigning tasks, following up with owners, and keeping all stakeholders updated with costs, timelines, and open risks.
- Relational data connects weaknesses to controls, policies, and frameworks so you know every element of your agency that is impacted.
What if we need help configuring POA&M process in Onspring?
Does FedRAMP require use of POA&M software?
The use of software to manage POA&M is not a legal mandate. However, businesses working under DoD contracts are required to comply with DFARS rule 252.204-7012 to protect controlled unclassified information. Ultimately, that compliance means a business must implement the cybersecurity requirements outlined in the National Institutes of Standards and Technology (NIST) 800-171 standard.
Within this standard, a business is required to systematically assess its cybersecurity risk, namely the risks associated with incomplete 800-171 compliance. Additionally, the business is also required to instill a Plan of Action and Milestones (POA&M), identifying steps that the business will carry out to mitigate those incomplete 800-171 risks.
Due to the complexities, timelines and budget, automating your POA&M management with Onspring software is often the most efficient way to streamline workflows, reporting and documentation.
Can our organization escalate issues and see all efforts underway to close and address risks?
Yes. Onspring dashboards provide a consolidated view into all issues, which include reports to segment risks by level so your team can take a risk-based approach to issues triaging and prioritization.
Automated triggers in Onspring can also be used to notify team members when high-risk weaknesses are logged. This functionality provides immediate visibility to escalate issues for remediation.
How does Onspring’s POA&M software reduce costs or enable faster reactions to emerging risks?
On average, customers experience 40% time savings when using Onspring and prevent hundreds of thousands of dollars in fines and costs from security deficiencies. We provide:
- Always-on live reporting eliminates time spent aggregating and formatting data for reports.
- Automated project management eliminates time spent assigning tasks, following up with owners, and keeping all stakeholders updated with costs, timelines, and open risks.
- Relational data connects weaknesses to controls, policies, and frameworks so you know every element of your agency that is impacted.
-

What Is an IT Security Audit? A Guide to Security Audits & Best Practices
Unlock the power of process automation without compromising security. Learn how audits uncover risks, ensure compliance, and build stakeholder trust. Get best practices for secure audits using automation and third-party assessments.
-

Risk Exception Management: Creating a Policy Exception Process
Navigating corporate policies can be tedious, especially when exceptions are needed. Discover how to balance policy adherence with real-world flexibility for risk exceptions while mitigating risks effectively.
-
Reporting Best Practices: Using Color to Communicate Data
Learn how the right use of color in charts and graphs turns your reports into powerful decision-making tools.
