In any risk management program, a risk register stands as an indispensable tool. It’s your go-to resource for identifying, assessing and tracking risks within your organization. For risk managers wanting to create a risk register for their organizations, the art of building an effective risk register will positively affect and mature the broader impact of your risk management efforts.
To gain a better understanding of what a risk register is, why it exists and what information it should contain, Onspring’s VP of Client Services, Evan Stos, shares his consulting experience in governance, risk and compliance (GRC), helping more than 60 Fortune 500 companies gain control of audit, risk, compliance and information security processes.
What Is a Risk Register?
Where To Create Your Risk Register
How To Build a Risk Register
Step 1: Identify and Define Risks
Step 2: Assess Risk Impacts
Step 3: Assign Risk Ownership
Step 4: Develop Risk Response Plans
Step 5: Monitoring and Maintaining Your Risk Register
What Is a Risk Register?
The purpose of a risk register is to allow you to see all of your potential risks in one place, to prioritize those risks and assign ownership, and to plan to respond to them in some way.
“Risks can pop up all over the organization,” Stos shares, “and if you don’t have a mechanism to capture and track them, you’ll never have a clear picture of risk (and potential business consequences) from a management perspective.”
Your risk register will be the centralized repository that captures all identified risks along with their severity, potential impact on future projects or current operations, mitigation strategies (or action plans) and status updates. Think of it as your organizational crystal ball—offering foresight into potential pitfalls while providing actionable insights for mitigation.
Key Components of a Risk Register:
- Risk Identification: Cataloging possible risks
- Risk Assessment: Evaluating risk likelihood and potential adverse impacts
- Mitigation Strategies: Outlining action plans to address each identified risk
- Monitoring and Review: Keeping tabs on new risks over time
Where To Create Your Risk Register
Plenty of organizations get by with a simple Excel spreadsheet, but you may know from experience just how quickly a spreadsheet can go from organized to overwhelming. Plus, they are prone to human error and there may be issues with version control.
When you’re learning how to create a risk register and if you want to future-proof your new risk register, the best way is with specialized software that will save your team from the onerous task of manually updating spreadsheets while still keeping everyone informed and accountable to their own piece of the risk-management pie.

How To Build a Risk Register
Step 1: Identify and Define Risks
The first step in building a robust risk register involves identifying all possible risks that could affect your organization or specific projects. This requires collaboration across different departments to ensure no stone is left unturned.
“In an ideal world, anyone in the organization could establish a risk, which would then go into a review process to determine its validity,” Stos says. “But in reality, it’s typically the enterprise risk management (ERM) office that’s interfacing with different areas of the business to draw out information and capture it in the risk register.”
Techniques for Identifying Risks:
- Brainstorming Sessions: Gather cross-functional teams to brainstorm potential risks.
- SWOT Analysis: Evaluate strengths, weaknesses, opportunities, and threats.
- Historical Data Review: Analyze past incidents or near-misses for recurring patterns.
- Industry Benchmarks (e.g., NIST): Study common cyber security risks within your industry sector.
Document each identified risk with sufficient detail so that it can be easily understood by anyone reviewing the register. Include elements like brief descriptions and relevant parties involved.
Building the structure of your register in a tool will vary by company and by tool, but often each identified risk is defined by this information:
- Name: A title and description with sufficient detail to understand what the risk is and how it could impact the organization
- Owner: An assigned risk owner and manager/delegate who will be responsible for monitoring and responding to the risk (more on this in step three)
- Category: A keyword that sums up the type of risk, such as strategic, financial, reputational, operational, IT or compliance
- Score: The likelihood that the risk could occur and the potential impact the risk could have on the organization, typically measured on a 5×5 scale (more on this in step five)
- Contributing factors: What causes (or could cause) the risk to occur, which is not always known
- Response plans: How you’re going to respond to the risk, which is also called “risk treatment” (i.e., mitigate, accept, transfer or avoid)
In an automated risk management tool, you can relate and cross-connect other data points that give a fuller, richer picture of each risk, such as:
- Related objectives, processes and assets
- Supporting controls
- Risk metrics (key performance indicators and key risk indicators)
- Related mitigation plans
- Incidents of past risk occurrence (if any)
Step 2: Assess Risk Impacts
Once you have a comprehensive list of possible risks or "risk-bearing events,” the next step involves assessing each one in terms of its likelihood (risk probability) and potential negative impact on your organization or project plan. This assessment helps prioritize high priority risks requiring immediate attention versus those that can be monitored over time.
Methods for Assessing Risks:
- Qualitative Assessment: Use descriptive scales (e.g., high/medium/low) to evaluate likelihood and impact.
- Quantitative Assessment: Apply numerical values or statistical models where possible using data security metrics.
- Risk Matrix/Common Scale: Create a matrix plotting likelihood against impact to visualize priority levels clearly.
Ensure consistency in how assessments are conducted to maintain reliability across different types of common risk categories. Depending on your risks, you may also want to incorporate scoring and live intel from other data sources or continuous monitoring subscription services. For example, a financial institution might integrate continuous monitoring services to track real-time scoring for cyber threats.

Step 3: Assign Risk Ownership
Every risk needs an owner, and it’s usually two or three layers deep. “First, you have the actual ‘risk owner,’ who's typically an executive responsible for managing and controlling identified risks. This is the big-picture person,” Stos explains. “Then you have a ‘risk manager’ or ‘risk delegate’ who is responsible for keeping tabs on the risk. That’s the detail person.”
This multilevel ownership format means risk owners and managers are not typically your chief risk officer or VP of risk management (though for global, company-wide risks, they can be). In most cases, the owners and managers are out in the lines of business, deeply involved in the projects and processes where risks arise. By contrast, the CRO or VP of risk management is responsible for leading enterprise-wide identification, analysis and response to risks.

Step 4: Develop Risk Response Plans
Once you’ve assessed your risks and have owners responsible for managing those risks, you’re ready to strategize your organization’s risk responses. Risks with the highest severity scores are most likely to have the most significant adverse impacts to your organization. Response plans for these risks should be prioritized for strategies aimed at mitigating these threats quickly and fully. Robust mitigation plans should outline specific actions required to reduce either the likelihood or severity (or both) of each identified threat.
Crafting Mitigation Plans:
- Preventive Actions: Steps taken to prevent occurrence (e.g., implementing stronger controls).
- Contingency Plans/Risk Work: Backup plans activated if preventive measures fail (e.g., disaster recovery protocols).
- Ownership Assignment/Key Stakeholders Involvement: Designate responsible individuals such as senior leaders or specialized teams for executing mitigation actions effectively within set project timelines.
Document these strategies clearly in your risk register alongside each corresponding entry under sections like "risk description" or "risk breakdown structure."
“When it comes to reporting on risk, a popular format is a risk heat map, which is typically a 5×5 scale with impact on the X-axis and likelihood on the Y-axis,” Stos advises. “This allows you to plot risks and quickly identify those that require prioritized attention.”
Once you’ve begun working to mitigate these risks, you may want to switch to working across multiple heat maps. That way, you can separately track residual risk — whatever risk remains after some kind of response — and inherent risk, which means no response actions have yet been taken.
Step 5: Monitoring and Maintaining Your Risk Register
Learning how to create a risk register in a static spreadsheet might be a good practice area, but it quickly becomes obsolete when emerging threats continually move. That’s why we recommend monitoring risk in an automated tool. If you have some sort of process risk management technology in place for your risk register, you can automatically notify risk owners either by a set trigger or on a set schedule to review risk information. The tool can attest that they’ve looked at the information and note any material changes, which is all captured in your risk register.
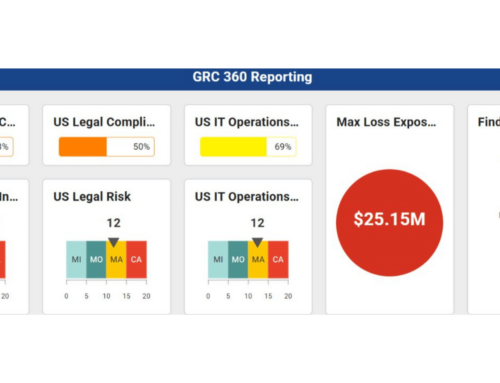
Executive management will also want to periodically review the organization’s risk landscape, with an emphasis on the most significant risks. Dashboard reporting shows upper management where the organization may have problems and what’s being done to address them.
“Accurate reporting from the risk register enables management to make informed decisions,” Stos explains. “Without a current, accurate risk register, management is not operating from a place of confidence. That’s why a risk register with clearly defined risk ownership is so crucial. It takes an investment of time and resources to keep a risk register up to date, but I’ve never seen a situation where it wasn’t worth the effort.”

Effective Monitoring Practices:
- Scheduled Reviews: Set regular intervals e g quarterly comprehensive reviews
- Real Time Tracking Tools: Utilize software solutions offering real-time updates statuses
- Feedback Loops: Encourage active participation feedback loops among stakeholders managing specific areas ensuring emergent threats swiftly addressed existing ones remain controlled
Read more: Risk Management E-Book: 6 Reports for No-Hassle Risk Management

Conclusion
Learning how to create a risk register helps build a proactive culture focused on understanding and mitigating risks before crises occur.
By following this step-by-step guide—identifying risks, comprehensively assessing them, systematically developing robust strategies, maintaining vigilance, and monitoring continuously—you'll enhance your foresight and resilience against future uncertainties.
If you’re struggling to establish or maintain an accurate and comprehensive risk register for your organization, we’d love to help. Let us know if you’d like to take a closer look at Onspring risk register.