Four Workflows to Help Prevent Third-party Data Breaches

More than half of organizations surveyed by the Ponemon Institute have experienced at least one data breach caused by a third party. So what kind of company does your data keep?
While you might have good risk management activities in place, like penetration testing, security questionnaires, SOC reporting, etc., you’ll gain best-in-class visibility and control when you do these activities in conjunction with risk ratings in a GRC platform.
That’s why there’s the data connector for SecurityScorecard in Onspring.
SecurityScorecard provides a comprehensive cyber security risk score for each of your vendors plus cybersecurity health ratings across 10 groups of risk factors. Their proprietary algorithms tally these metrics into an easy-to-read, A-F security rating based on company risk findings.
Always current, this integrated data enables you to continuously monitor changes in your own cyberhealth as well as the cybersecurity posture of everyone in your third-party ecosystem.
This data means you’ll finally be able to scale with your every-expanding vendor ecosystem.
So bring that into Onspring and what happens? Security administrators get alerts, triggered plans and communications for due diligence, faster remediation as well as the ability to prove continuous compliance to standards & frameworks. It’s a beautiful thing.
When you finally have visibility, flexibility and speed accelerating your vendor management or third-party risk program in Onspring, things like automated workflows and responses become your undeniable allies in preventing and mitigating cyber security risks.
Let’s take a look at a few TPRM workflow examples.
Traffic Cop Workflow
You can automate security ratings to pinpoint required activities and depth. How? Take your rating components and map them to other activities, like a questionnaire or pen test. Then establish a Go, No Go or Partial Go threshold.
This means you’re only going to fire the activity if the threshold is tripped, which also simultaneously adjusts timed assessments accordingly—and avoids unnecessary ones.
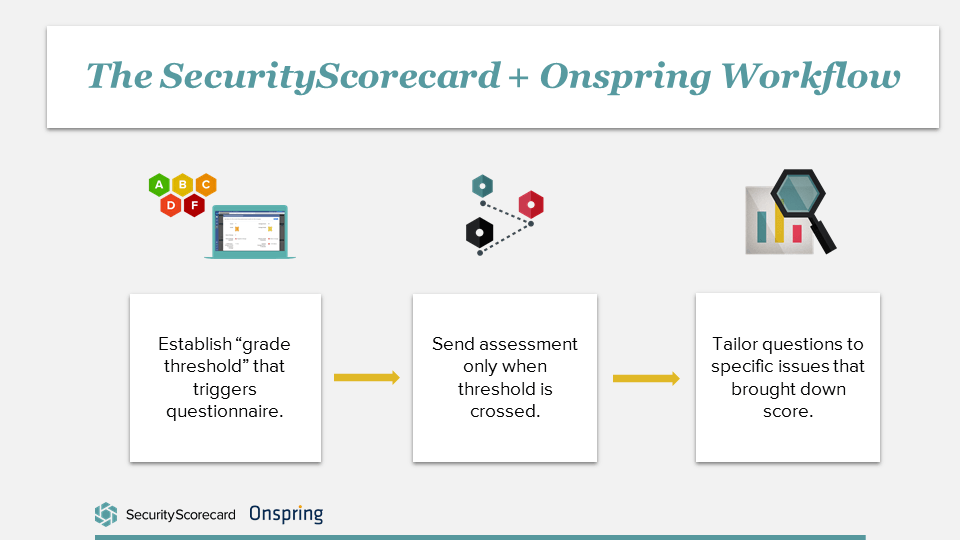
Let’s say we’re only going to run a penetration test when the score falls below a B. (This is already a win because we’ve avoided unnecessary and costly pen tests.) And of those, we’re only going to test when vectors that map to factor scores fall below a C.
So instead of testing everything that we can get our hands on, we are focusing specifically on the things that trip the wire in the first place.
It’s a just-in-time assessment that’s right-sized because you get clear focus on the real, pertinent issue, not the kitchen sink.
Low Tier Workflow
This is based on the risk-reward concept. If a vendor’s risk consequences to you are minimal, there’s no need to waste excessive effort on assessing them.
So streamline those low-tier vendor assessments using grades as a compass. Establish a pass/fail threshold that allows you to prioritize quickly which assessments will yield the most value.
Backlog Workflow
Have a backlog of inherent risk assessments? Prioritize them based on data from ratings. The big goal here is to have eyes first on high criticality vendors with poor security.
We know we can’t take a proxy for inherent risk because it’s a function of the relationship and use case. However, there is a direct proxy for security with SecurityScorecard ratings.
So if you were to sort the backlog from low grade to high grade, you’re already guaranteeing that you’re going to have eyes earlier on those high-risk, low-security vendors.
Collaboration Workflow
We know third-party risk management is more than just grading. As a result of our connectedness, vendor risk is a problem that’s too big to solve for any one company. That’s why working together to resolve issues and restore cyber health is really the goal.
When a vendor trips a threshold, SecurityScorecard gives you the right to share score visibility with vendors and send a questionnaire relevant to that issue.
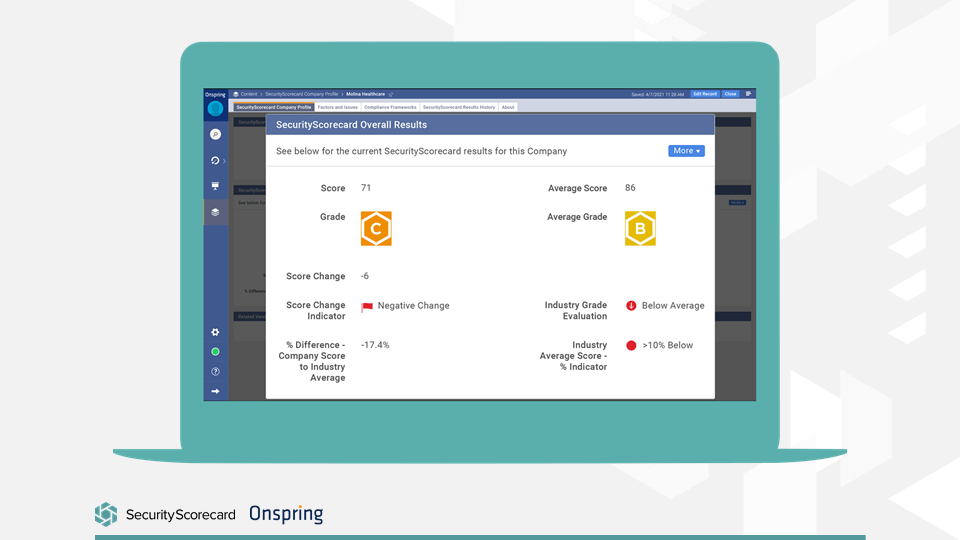
This opens up a dialogue. It also means both parties are seeing the same information to work together to improve risk posture. It’s about building relationships instead of pointing fingers.
This opens up a dialogue. It also means both parties are seeing the same information to work together to improve risk posture. It’s about building relationships instead of pointing fingers.
The Big Takeaway about Cybersecurity Risk Ratings
When you power automated workflows and live reporting in Onspring with actionable cybersecurity data from SecurityScorecard, you can scale your risk management program with deeper insights and quicker action.
The next step is to see how SecurityScorecard in Onspring could work for your specific use case. We’re happy to show you.





