The Key to Proactive Third-Party Risk Management?
Continuous Data Monitoring
As part of our vendor risk Q&A series, we talked with Matthew Ancelin, principal solutions architect at SecurityScorecard, to discuss vendor risk management trends and how organizations can stay on top of third-party vendor risk.
SecurityScorecard rates the cybersecurity footprint of over 12 million entities globally, giving an A through F grade through proprietary, continuous monitoring. Organizations use an entity’s cybersecurity grade to analyze risk stemming from contracted third parties. The rating data gives companies more predictive information for likelihoods and breaches. Onspring feeds SecurityScorecard cybersecurity data into risk management and third-party/vendor risk management products. With this data feed, score changes can activate assessments, remediation activities, and communication plans across teams.
Matthew provides valuable insights on the importance of end-to-end risk management and discusses how to incorporate cybersecurity data into your risk management program.
Could you tell us a little bit about SecurityScorecard?
SecurityScorecard is a cybersecurity credit check on companies. You perform a credit check to determine if your company should extend credit to another company. Now think about security ratings as that credit check for companies. We perform a security check on any company our customers are looking to share sensitive data with—to build confidence in that relationship or alert them of any red flags before sharing that data. Our security ratings are brought to customers with an A through F grade. A is good, F is bad.
To determine a company’s security rating, we collect public information by crawling the internet and approaching an IP address or by obtaining public documents, sources, etc. SecurityScorecard gives companies very detailed technical information and provides insight into threat actor connections, which identifies any vulnerable connections.
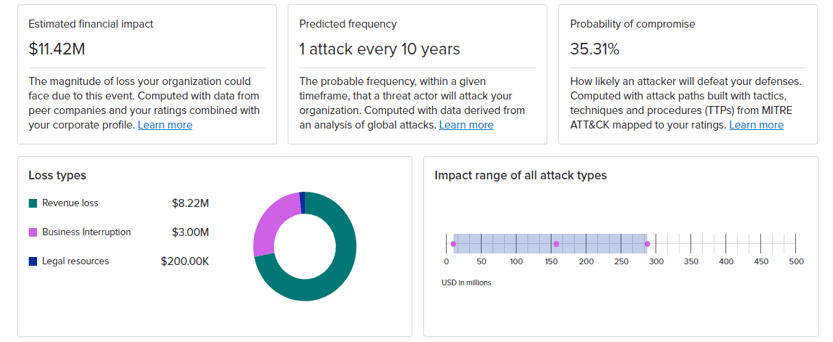
For example, SecurityScorecard in Onspring can help you uncover if particular threat actors are involved with an incident that you may be involved in. You can then reach out to the source and let them know, “Hey, one of your web servers has gotten repurposed by the bad guys. And now it’s attacking me. So, you might want to take a look at that.”
This kind of data in your GRC system offers a much quicker time to resolution when you have that kind of intelligence at your fingertips.
Folks find security ratings very valuable in prioritizing which of their vendors may need the most attention. Risk management has evolved quite a bit, so we’re seeing additional technologies and data being used to measure risk and act on it, such as:
- Attack surface intelligence
- Automatic vendor detection
- Cyber risk quantification
- Internal security suite
And SecurityScorecard uses these emerging technologies alongside traditional security ratings to fully analyze a vendor’s risk.
Why is managing supply chain risk from a cybersecurity perspective so important?
Twenty years ago, you kept all of your data inside buildings—inside of firewalls—and protected it there. But we live in the age of cloud enablement, and everyone’s data is outside their four walls. So, the question becomes about trust: Can I trust this other company to be a good steward of my data?
Recently, there have been some big cyber hacks, such as the SolarWinds event. This was a prime example of what a supply chain breach can do to a company. It’s not enough anymore to build a big front door with walls around it. You also have to be very aware and manage the risk of the third parties with which you’re working and sharing sensitive data.
When it comes to risk management, who “owns” that role?
Whenever a technical risk gets brought up, such as cybersecurity, the IT or security team tends to jump in because they know the process and have the subject matter expertise. But when you have a larger company, there tends to be more leadership happening in the risk management world, so there might be a dedicated risk management team or department. What I would say in this case, when it comes to ownership, is that the risk management team is the one doing disaster risk modeling or financial risk modeling, so they’re owning it from that perspective. But it’s always helpful to collaborate with subject matter experts. In this example, it would be the IT department, and in doing so, you can proactively eliminate any risk the proper way.
If an organization is new to formalized risk management, where do they start?
It really depends on the regulatory concerns and size. For example, if you’re a part of a large company with enough regulatory concern that it’s important to start your own program, the best place to start is in finding a GRC platform, such as Onspring.
If you’re managing vendors, vendors have the same contact info as your family or your customers: names, phone numbers, email addresses, etc. So, you need to have an organized place to store that information in an easy-to-digest format. Spreadsheets are often the first format people look to organize this, but this involves manual updates, which will ultimately lead to bad data, poor data collection techniques, and so on.
The next step in formalizing your process, one that we’ve seen from our customers, is going from point-in-time checks—questionnaires, pen tests, etc.—to continuous data monitoring.
And this is extremely important. I’ll use COVID as an example. Looking at some of our ratings, there were many mid-sized companies that scored an A or a B prior to COVID, but when the pandemic hit, they didn’t have extensive remote access set up, so they were scrambling to quickly set it up. But this caused tons of exposures. There was an uptick in the amount of remote desktop protocol facing the internet, which meant that some attacker was able to just guess the right username and password and have complete control of a machine inside that company. So, it’s important to keep tabs on your data and security vulnerabilities at all times to proactively avoid problems like these when you’re forced to make a split-second decision.
It’s not enough to look once a year or mid-year because when a crisis like COVID occurs, you need to know that your vendors don’t pose a risk to your business. And if you are worried about your data, you need to take proactive steps to pull it away from that vendor and lock it or encrypt it. This way, no matter the likelihood of them getting breached, your data is safe. It also shows that vendor that you’re serious about risk because it could cost you and the vendor thousands of dollars in damage if action isn’t taken.
How do you get that early warning system? Continuous monitoring is what can give you that.
If you’re looking for ways to incorporate cybersecurity ratings into your third-party vendor risk management program, drop us a line at hello@onspring.com.
Onspring’s comprehensive GRC Suite helps you manage compliance frameworks, automate data management, and continuously track and monitor risk, to name a few. With Onspring, businesses of all sizes and in all industries can make managing risk simpler and more efficient. No matter the stage of your risk management maturity.
Actionable insights we think you’ll like
6 Benefits of Using Vendor Risk Assessment Software
From minimizing disruptions to empowering teams with actionable insights, learn how tools like Onspring and Black Kite enhance efficiency and security.
Top 5 Ways that a GRC Portal Simplifies Third-Party Risk Management
Investing in GRC automation technology often benefits power users, but what about occasional users like leaders, contributors and vendors? A well-designed GRC portal can make a world of difference.
Creating Your Vendor Management Policy
If you don’t create an all-inclusive vendor management policy, you’ll be bogged down with unending third-party management chaos triggered by different vendors.







